Cortex
Speed up analysis and make response easier
This powerful engine is the essential open-source companion for TheHive.
It allows you to analyze tens, if not hundreds of observables
at once and trigger active responses in just a few clicks.




































The magic at TheHive’s side
Step up your analysis
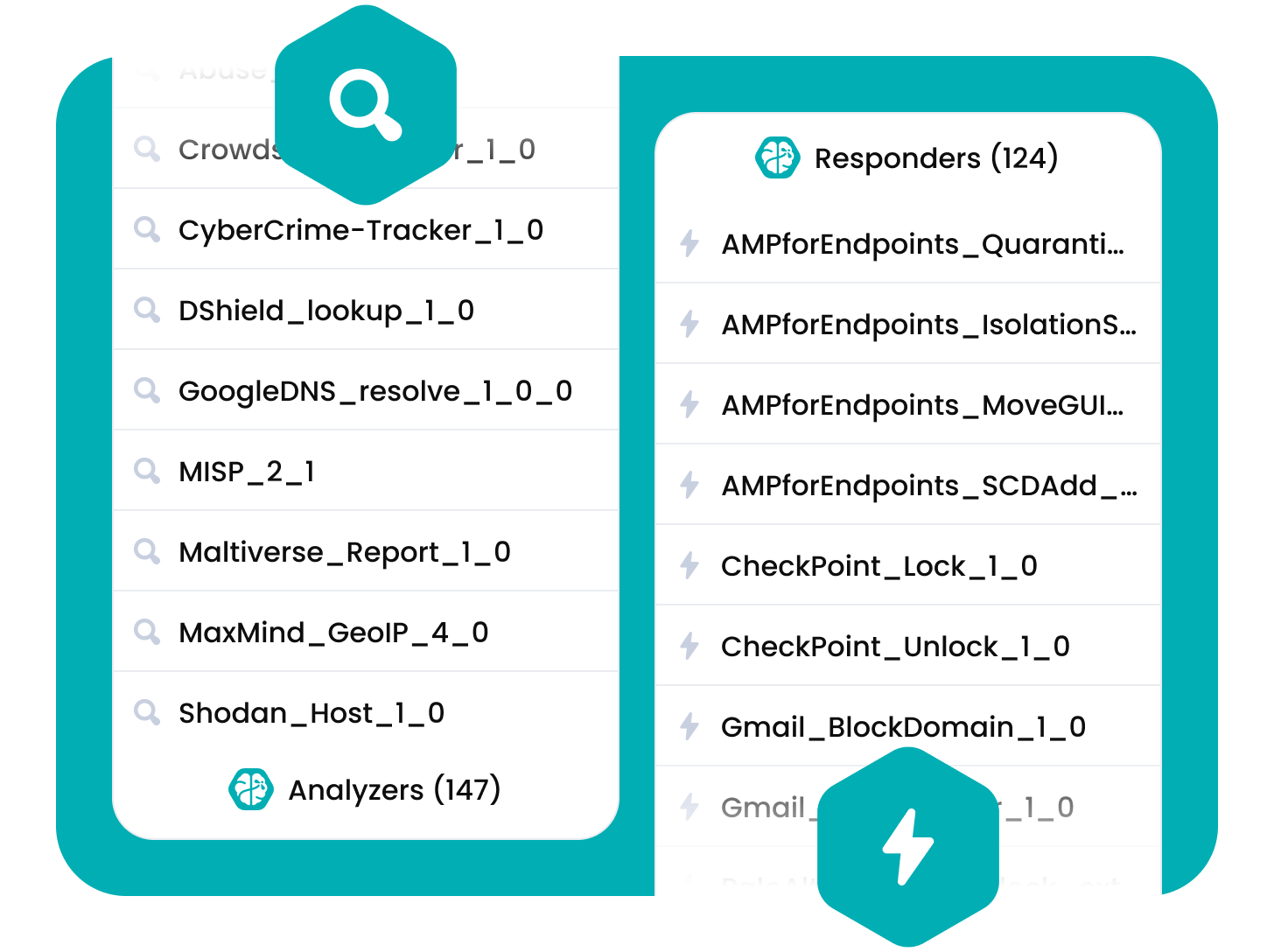
- Leverage more than a hundred trusted analyzers for popular services such as VirusTotal, Joe Sandbox, DomainTools, PassiveTotal, Google Safe Browsing, Shodan and Onyphe.
- Identify abuse contacts, parse files in several formats such as OLE and OpenXML to detect VBA macros, generate useful information on PE, PDF files, and much more.
- Submit large sets of observables from TheHive, custom scripts or MISP.
- Query Cortex analyzers from MISP to enrich events and extend the coverage of your investigations.
Own it
- Enable analyzers that allow to query your legacy and 3rd-party services using your own settings and user credentials.
- Create your own responders based on your active response workflows and processes.
- Easily parse Cortex output and display it the way you want using TheHive’s report engine. Cortex can also be interfaced with other products through its REST API or by using Cortex4py.

300+ integrations






























Cloud Images (IaaS)
Use Cortex as a separate open-source analysis & response engine, benefit from it coupled with TheHive, or get the most out of it in the IaaS format.
Work with images on your preferred cloud platform while we help with the essentials like deployment, configuration, updates and maintenance.
What our users say
GM, Global Cyber Operations EU, BT Business
Cybersecurity architect, Bureau of Information and Telecommunications, State of South Dakota
CERT / CSIRT, ARKEA
Software industry
Education industry
Manufacturing industry
IT services industry
IT services industry
IT services industry
Insurance (except health) industry
Transportation industry
Construction industry
Education industry
Software industry
Miscellaneous industry
Miscellaneous industry
IT services industry
Banking industry
Miscellaneous industry
Miscellaneous industry
Miscellaneous industry
Miscellaneous industry
Cybersecurity analyst, CERT Gemalto
Miscellaneous industry
Get started with Cortex
Join the global community of security professionals who investigate incidents more efficiently than ever with our engine.
Frequently Asked Questions
Other questions?
StrangeBee is happy to help! Get the answers directly from our experts.
Yes, and it’s available here.
Cortex is free. We are, however, at your service in case you need support for a deployment or training.
Nothing has changed. TheHive 5 and Cortex continue to be an excellent combination.
Your Cortex servers will remain functional.
Don’t worry, your analyzers and responders will remain hard at work!